The 5 Most Common Types of Air Gap
- Kiera Quinn
- -
- Bare Metal Automation
In bare metal environments, air gap is often treated like a binary — either you’re connected or you’re not. But in practice, there are multiple levels of separation, and understanding where you sit on that spectrum is essential for system design, audit, and operations. Prefer a video? We made a YouTube short covering these air gap models.
The Most Common Air Gap Configurations
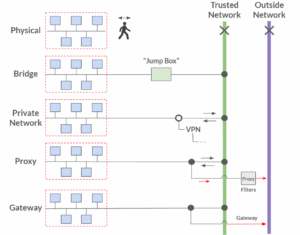
1. Physical Air Gap
This is the most extreme form of isolation, a true air gap. There’s a complete physical break between your infrastructure network and any outside or trusted network. Data is moved by physically carrying it in or out using portable storage.
Use Cases: This is common in high-security cases like military or national security.
Benefits: This setup allows for maximum security and control.
Drawbacks: Slower manual processing required for every update or package.
This is the model people usually picture when they hear air gapped. It’s rarely used in enterprise settings.
2. Bridge via Jump Box
A jump box serves as a bridge between your trusted network and the isolated infrastructure. It’s an intermediate server that admins log into to fetch updates or transfer files into the restricted environment.
Use Cases: This setup is ideal when you need electronic transfers but still want a degree of control and separation. This is common in secure enterprise environments where fully manual processes are too slow, but open access is too risky.
Benefits: This setup enables controlled file transfers. The jump box choke point makes it easy to log transfers and audit the interior infrastructure.
Drawbacks: The chokepoint can create a single point of failure, if the jump box goes down you have no access to your isolated infrastructure.
Best Practice: Keep the jump box dedicated to this function. Don’t overload your control server or provisioning system with this role. Separation reduces risk and simplifies audit.
3. Private Network
In this model, your infrastructure has no access to the internet, but it’s fully reachable from your trusted internal network, often over a VPN. Admins can connect freely through the VPN, but the systems themselves can’t reach out to fetch packages or updates.
Use Cases: This is one of the most common enterprise setups. It’s easy to manage for internal teams but still provides meaningful isolation from untrusted networks.
Benefits: This setup is good for teams of infrastructure engineers
Drawbacks: Without a choke point, it is harder to audit the internal infrastructure network.
This model strikes a balance between usability and restriction. However, the lack of a chokepoint can lead to hidden access risks.
4. Proxy-Controlled Access
In this configuration, outbound requests are possible but extremely limited. Instead of direct internet access, infrastructure traffic flows through a managed proxy. The proxy filters requests, enforces strict rules, and often allows access only to whitelisted domains or services.
Use Cases: This is a common model for many enterprise networks that need limited outbound access without exposing the entire infrastructure.
Benefits: This is functionally the same as having no internet access except for the trusted list of providers.
Drawbacks: The whitelisting process can be slow. The proxy can also be sensitive to API changes and can drop requests if they aren’t made exactly according to the proxy’s rules.
In practice, a tightly restricted proxy can feel just as limiting as a full air gap. If your systems rely on external services, expect to do extra work to make them proxy-compatible.
5. Outbound-Only Gateway
In this air gap setup, systems can initiate outbound connections to the internet via requests, but inbound traffic is still limited. Typically this is done through a firewall-controlled gateway.
Use Cases: Great for test environments or dev labs where engineers need flexibility without fully opening the door to inbound traffic.
Benefits: Full outbound access is allowed. This allows for a large degree of flexibility while still maintaining security.
Drawbacks: It’s harder to monitor and control what’s being accessed.
While convenient, this model is uncommon in enterprise environments. Most organizations elect for more secure air gap methods.
Decide on Your Air Gap Before You Deploy
Understanding your air gap isn’t just good practice, it’s critical infrastructure hygiene. It’s best to choose the air gap configuration that works best and build your environment based on that. Your environment’s connectivity model will shape what works and what breaks. Knowing your air gap type means fewer surprises and faster recovery.
Want to learn more about automating in air gapped environments? Schedule a meeting with our infrastructure automation experts.



